LDAP Bridge
Last Updated: 17 Nov 2021
The LDAP Bridge asset is used to interface to an LDAP directory, which can be either OpenLDAP or Active Directory. Users will then be able to log into the system by using their LDAP username and password. You can also use LDAP users in Workflow Schemas, Permissions and Roles.
Adding an LDAP Bridge
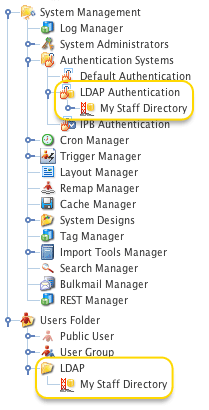
Example LDAP Bridge
To add an LDAP Bridge, in the Add menu go to LDAP -> LDAP Bridge. You can create an LDAP Bridge anywhere in your system where User Groups are allowed. To allow users to log in using their LDAP accounts, however, it needs to be linked under the LDAP Authentication asset. For example, the figure to the right shows an LDAP Bridge called My Staff Directory, which has been created under the User Folder and linked under the LDAP Authentication asset. By doing this, it allows users, who are not System Administrators, to access your LDAP directory so that they can change Permissions, create and apply Roles and create Workflow Schemas.
Once you have created your LDAP Bridge , you can configure the asset on its associated screens. Many of these screens are the same or similar to those for a Standard Page and are described in the Asset Screens manual. In this manual we will only describe the Details, Attribute Setup and LDAP User Setup screens, which are different for a LDAP Bridge.
Steps to Setting Up a LDAP Bridge
To set up an LDAP Bridge, perform the following steps:
- Create a LDAP Bridge. If you do not create it under the LDAP Authentication folder in the Asset Map, make sure that you link it under this folder. For more information, refer to the Adding an LDAP Bridge section above.
- Enter the connection details for the LDAP directory on the Details screen of the LDAP Bridge. Once you have entered the details and clicked Commit, the Connection Status should change to Connected. If it does not change to Connected, the details you have entered may be wrong. For more information on this screen, refer to the Details Screen chapter.
- On the Attribute Setup screen, enter the user and group attributes. For more information, refer to the Attribute Setup Screen chapter.
- On the LDAP User Setup screen, select any additional attributes that you want to use. For more information, refer to the LDAP User Setup Screen chapter.
- Change the Status of the LDAP Bridge to Live. Users can now log in using their LDAP username and password.
If a LDAP Bridge is not linked under the LDAP Authentication folder, Users will not be able to login.
Status of an LDAP Bridge
Once you have set up a LDAP Bridge, you need to change its Status to Live so that users can log in. If the LDAP Bridge is Under Construction it is considered inactive and users will not be able to log in.
Ordering LDAP Bridge Assets in the Asset Map
If you have created multiple LDAP Bridge assets in your system, the order of these assets in the Asset Map is important. When a user logs in using their LDAP account, Squiz Matrix will check each LDAP Bridge for their account details in the order they appear in the Asset Map. As soon as it finds the correct account, it will use the settings for that LDAP Bridge only. For example, say you had three LDAP Bridge assets set up and they appear in the order A, B, C in the Asset Map. Bill Jones has an LDAP account in the B and C LDAP Bridge assets. When he logs in, Squiz Matrix will look through each LDAP Bridge, find his account in B and use the settings for that LDAP Bridge. It will ignore any settings that may have been applied with C. If, however, C appeared before B the Asset Map, it will use the C instead.
Using Users and Groups from the LDAP Bridge
Once you have created and set up an LDAP Bridge, the LDAP directory and its records will be displayed in the Asset Map. You can use these users and groups within the LDAP directory as you would Squiz Matrix user accounts and User Groups. You can also link LDAP users into User Groups within Squiz Matrix.
Please note that the functionality of the LDAP Bridge within the Asset Map has a limitation of 1000 LDAP records on a single level. For example, two groups containing 800 users each will both function correctly in the Asset Map while a single group containing 1600 users will not.
LDAP records that do not function in the Asset Map can be maintained using the Squiz Matrix backend search field. You can locate specific users and groups using the <bridgeassetID>:<userDN> format, allowing you to individually edit the permissions and roles of these records.
Troubleshooting the LDAP Bridge
If you are unable to see LDAP users or groups in the Asset Map, check the following things.
- On the Details screen of the LDAP Bridge, make sure that Connection Status field says Connected. If it does not say Connected, the connection details on the Details screen may be incorrect for the LDAP directory.
- On the Attribute Setup screen, make sure that you have entered the correct details for the user and group attributes.
- Make sure that the LDAP Bridge has been linked under the LDAP Authentication asset in the Asset Map.
- Make sure that the LDAP Bridge is Live.
- On the System Configuration screen, make sure that Enable External Authentication Systems is set to Yes.
How are Groups and Users Identified?
When Squiz Matrix looks for groups or users in LDAP, it identifies them by using the objectClasses outlined in the tables below. If a group or user in LDAP is not using one of these objectClasses, it will not be displayed in the Asset Map.
Groups
| objectClass | Attribute |
|---|---|
| organizationalUnit | ou |
| posixGroup | cn |
| group | cn |
| groupOfNames | cn |
| groupOfUniqueNames | cn |
| domain | dc |
| container | cn |
| organization | o |
| country | c |
Users
| objectClass | Attribute |
|---|---|
| organizationalPerson | cn |
| inetOrgPerson | cn |
| userProxy | cn |
Searching for LDAP Users
Because LDAP Users are shadow assets, you can't search for them in the same way as normal users or other standard asset types. However, you can directly go to an LDAP User's Details screen using the Quick Search tool by entering the asset ID of the LDAP Bridge, followed by the LDAP CN. For example:
123:CN=bbanda,OU=Staff,O=Squiz,C=au,DC=ademo,DC=squiz,DC=net
Alternatively, if you are using the Use User ID as Shadow ID setting on the LDAP Bridge, you can simply enter the bridge asset ID followed by the username:
123:bbanda
