Federated Access Management
Last Updated: 19 Aug 2019
Federated access management involves the management of a user's identity, stored across multiple systems, allowing users to use the same identification data to obtain access to each.
Security Assertion Markup Language 2.0 (SAML 2.0) is an XML-based standard for authenticating and authorising access to secure domains, that is, between an Identity Provider and a Service Provider. SAML 2.0 enables web-based authentication, providing federated access management through single sign-on and identity verification.
Squiz Matrix employs this federated access management model to provide authentication via SAML 2.0 Identity Providers using SimpleSAMLphp integration.
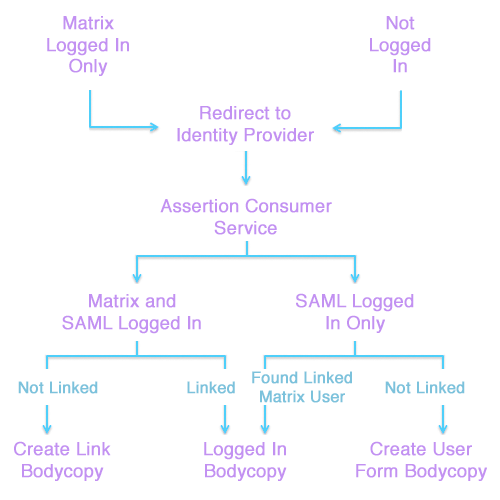
Federated access management within Squiz Matrix
When a user first accesses Squiz Matrix via the SAML Account Manager asset, they will be redirected to the SAML 2.0 Identity Provider for authentication. Once a user's identification has been validated by the Identity Provider, they will be redirected back to Squiz Matrix.
A user's Squiz Matrix account will be associated with the SAML identity, enabling federated access to the system, automatically signing the user into their account as part of the SAML authentication process. If no associated user account is found, the user will be able to either create a new account within Squiz Matrix to use for federated access or sign-in to an existing account to link to the authenticated identity.
SimpleSAMLphp Integration Within Squiz Matrix
In order for Squiz Matrix to provide federated access management, the SimpleSAMLphp application must be correctly configured and installed on the same server as your Squiz Matrix installation. Please refer to the SimpleSAMLphp Installation Guide for more information.
Squiz Matrix uses SimpleSAMLphp as a library, therefore, Apache web access of SimpleSAMLphp is not required and can be revoked once it has been configured and integrated with Squiz Matrix.
Once you have installed SimpleSAMLphp, edit the Squiz Matrix tools configuration file (located at data/private/conf/tools.inc), defining the directory path to SimpleSAMLphp, as follows:
define('SQ_TOOL_SIMPLESAMLPHP_PATH', 'path/to/simplesamlphp');Your Squiz Matrix system should now be correctly integrated with SimpleSAMLphp. You can verify this by creating a SAML Account Manager asset. The SimpleSAMLphp Status field should read Installed, as shown in the figure below.
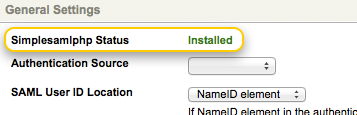
The SimpleSAMLphp Status field
For configuration steps for setting up SimpleSAMLphp as a Service Provider, see the SimpleSAMLphp Service Provider QuickStart Guide. Please note that configuration may differ depending on your Identity Provider. Refer to your IdP's Integration Guide for more information on setting up your SAML integration.
