Integration Setup: Feide Open IdP
Advanced
17 Dec 2015
This entire manual refers to a feature that was added in version 4.10.2
To understand how to integrate SAML federated access management, consider the following example of Feide Open IdP authentication integrated with Squiz Matrix.
- Ensure that SimpleSAMLphp is correctly installed on your Squiz Matrix system. For information on how to do this, refer to the Federated Access Management chapter in this manual.
-
Create a SAML Account Manager asset. The SimpleSAMLphp Status field should read Installed. If SimpleSAMLphp is Not Installed, you will need to review the installation of SimpleSAMLphp on your system.
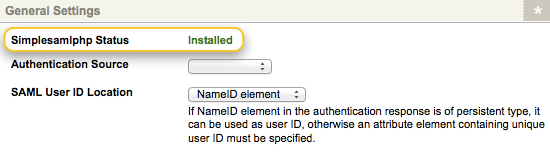
The SimpleSAMLphp Status field on the Details screen of the SAML Account Manager -
Next, provide import the metadata from the Feide Identity Provider. By default, the metadata for Feide Identity Provider is already included in the metadata distributed with SimpleSAMLphp. You can verify this by checking the saml20-idp-remote.php file on your SimpleSAMLphp installation within Squiz Matrix.
The Feide Identify Provider metadata required is available on Open IdP Feide and is as follows: -
Register an account on the Open IdP Feide site (https://openidp.feide.no/) and add a new Service Provider entity for integration with Squiz Matrix.
Once you have created a new Service Provider entity, you must supply it with the SAML 2.0 Service Provider metadata from the SAML Account Manager. To do this, insert the SAML Account Manager's Assertion Consumer Service and Single Logout Sevice URLs in the corresponding endpoint fields in the SAML 2.0 tab of your Service Provider entity settings on the Open IdP Feide site. These URLs can be found on the Details screen of the SAML Account Manager.
Alternatively, you can add a new Service Provider entity directly from SAML 2.0 XML metadata. The XML metadata of the SAML Account Manager can be accessed via the Service Provider Metadata Downoad URL field on the Details screen. -
Now that both the Service and Identity Provider metadata has been configured, the authentication source details of your Feide Open IdP entity must be added on the SimpleSAMLphp installation.
In the authsources.php field on your SimpleSAMLphp installation, add the following, replacing the entityID attribute with the name of the entity created on the Feide Identity Provider:// Add Feide OpenIDO authentication details
'feide' => array(
'saml:SP',
// The entity ID of this SP.
// Can be NULL/unset, in which case an entity ID is generated based on the metadata URL.
'entityID' => 'myentityid',
// The entity ID of the IdP this should SP should contact.
// Can be NULL/unset, in which case the user will be shown a list of available IdPs.
'idp' => 'https://openidp.feide.no',
// The URL to the discovery service.
// Can be NULL/unset, in which case a builtin discovery service will be used.
'discoURL' => NULL,
), -
On the Details screen of the SAML Account Manager, the Feide entity will now be selectable in the Authentication Source field. Select this option.
In the SAML User ID Location field, select the Attribute Element option, and then enter uid in the Attribute Element Name field, below. This will provide the SAML Account Manager with the a unique ID for users requiring authentication.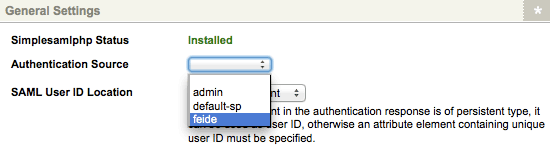
The Authentication Field on the Details screen of the SAML Account Manager
$metadata['https://openidp.feide.no'] = array (
'metadata-set' => 'saml20-idp-remote',
'entityid' => 'https://openidp.feide.no',
'SingleSignOnService' => 'https://openidp.feide.no/simplesaml/saml2/idp/SSOService.php',
'SingleLogoutService' => 'https://openidp.feide.no/simplesaml/saml2/idp/SingleLogoutService.php',
'certData' => 'MIICizCCAfQCCQCY8tKaMc0BMjANBgkqhkiG9w0BAQUFADCBiTELMAkGA1UEBhMCTk8xEjAQBgNVBAgTCVRyb25kaGVpbTEQMA4GA1UEChMHVU5JTkVUVDEOMAwGA1UECxMFRmVpZGUxGTAXBgNVBAMTEG9wZW5pZHAuZmVpZGUubm8xKTAnBgkqhkiG9w0BCQEWGmFuZHJlYXMuc29sYmVyZ0B1bmluZXR0Lm5vMB4XDTA4MDUwODA5MjI0OFoXDTM1MDkyMzA5MjI0OFowgYkxCzAJBgNVBAYTAk5PMRIwEAYDVQQIEwlUcm9uZGhlaW0xEDAOBgNVBAoTB1VOSU5FVFQxDjAMBgNVBAsTBUZlaWRlMRkwFwYDVQQDExBvcGVuaWRwLmZlaWRlLm5vMSkwJwYJKoZIhvcNAQkBFhphbmRyZWFzLnNvbGJlcmdAdW5pbmV0dC5ubzCBnzANBgkqhkiG9w0BAQEFAAOBjQAwgYkCgYEAt8jLoqI1VTlxAZ2axiDIThWcAOXdu8KkVUWaN/SooO9O0QQ7KRUjSGKN9JK65AFRDXQkWPAu4HlnO4noYlFSLnYyDxI66LCr71x4lgFJjqLeAvB/GqBqFfIZ3YK/NrhnUqFwZu63nLrZjcUZxNaPjOOSRSDaXpv1kb5k3jOiSGECAwEAATANBgkqhkiG9w0BAQUFAAOBgQBQYj4cAafWaYfjBU2zi1ElwStIaJ5nyp/s/8B8SAPK2T79McMyccP3wSW13LHkmM1jwKe3ACFXBvqGQN0IbcH49hu0FKhYFM/GPDJcIHFBsiyMBXChpye9vBaTNEBCtU3KjjyG0hRT2mAQ9h+bkPmOvlEo/aH0xR68Z9hw4PF13w==',
'NameIDFormat' => 'urn:oasis:names:tc:SAML:2.0:nameid-format:transient',
);
Your Squiz Matrix system has now been configured with federated access management with the Feide Identity Provider.
Preview the SAML Account Manager on the frontend to begin the authentication process. If you are logged into Squiz Matrix, you will prompted to link your account; if you are not logged in, the user creation settings will be displayed.
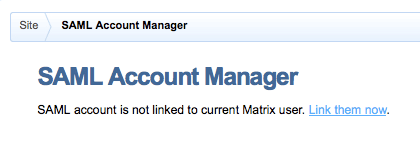
The Feide IdP authentication process on the SAML Account Manager
